学习学习Splunk
上班打CTF,有点意思哈~
开题页面如下:
Splunk官方提供的教程,美滋滋
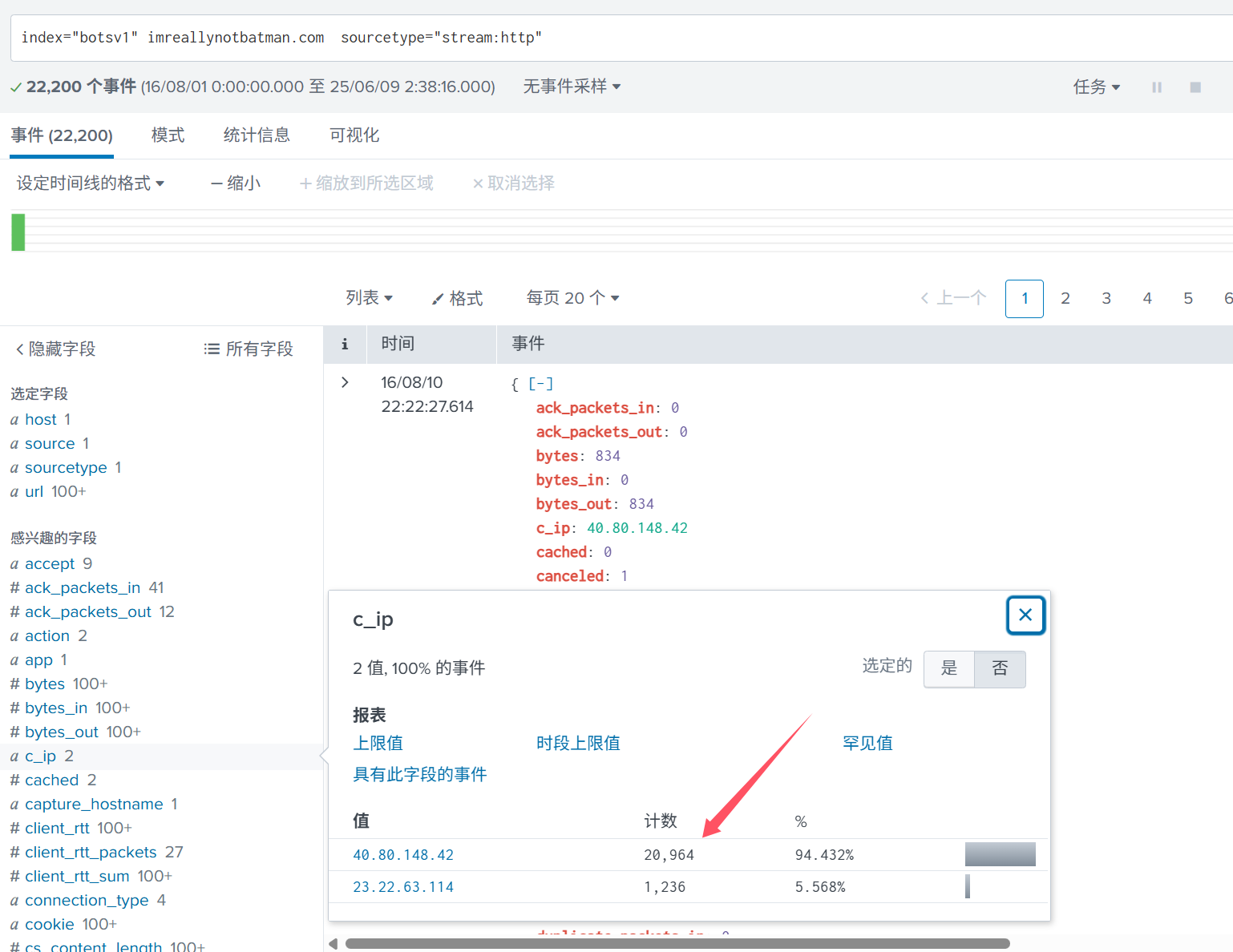
Q1: 扫描器源ip是多少?
打开看看数据摘要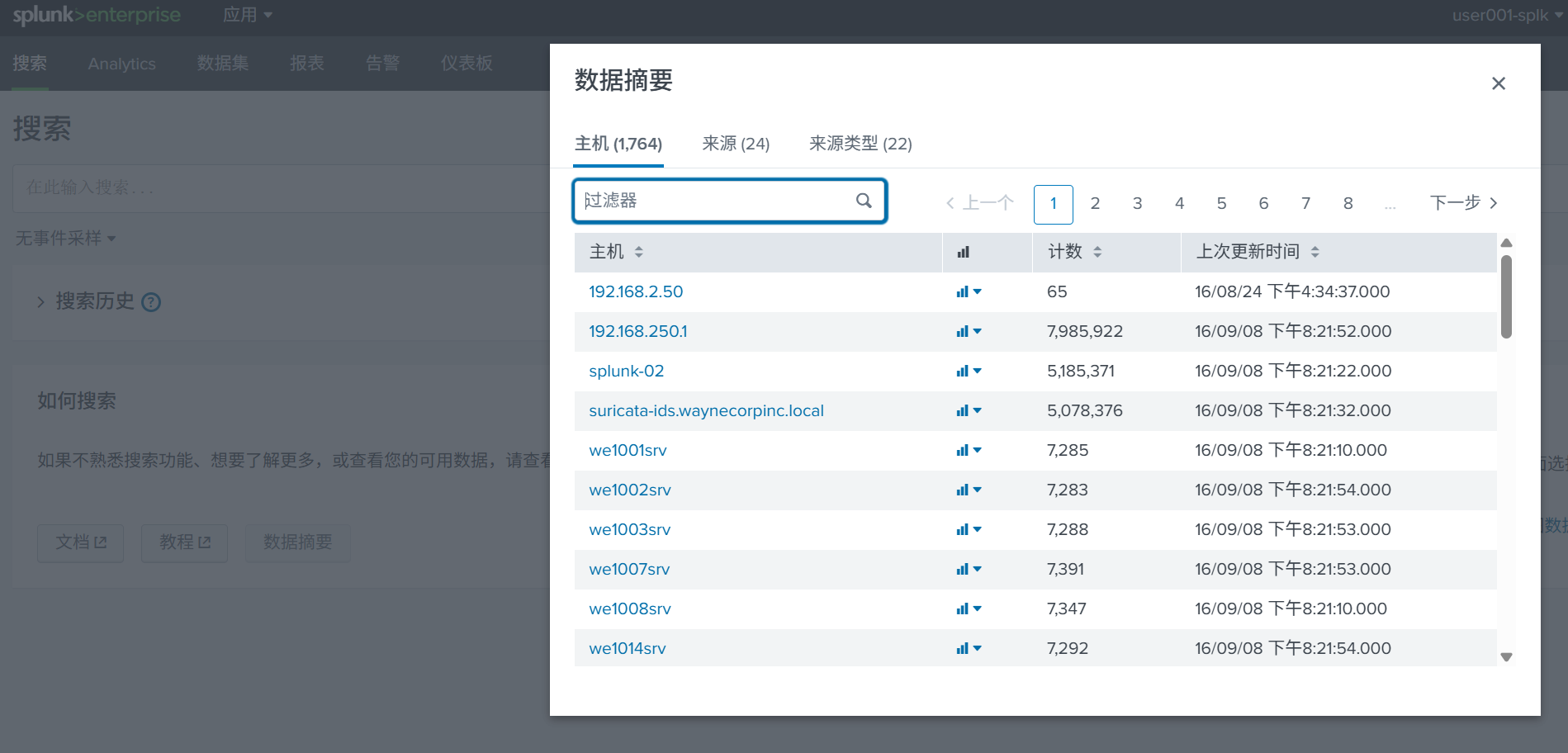
然后瞎几把乱交扣了二十分!,逆天负分数根据目录扫描的特征,发包次数很多且肯定是http协议,那么就先筛这两个再去看看源ip
优先提交次数多的即可.40.80.148.42
应该就是你了,不管先交~哈哈哈哈这次对了
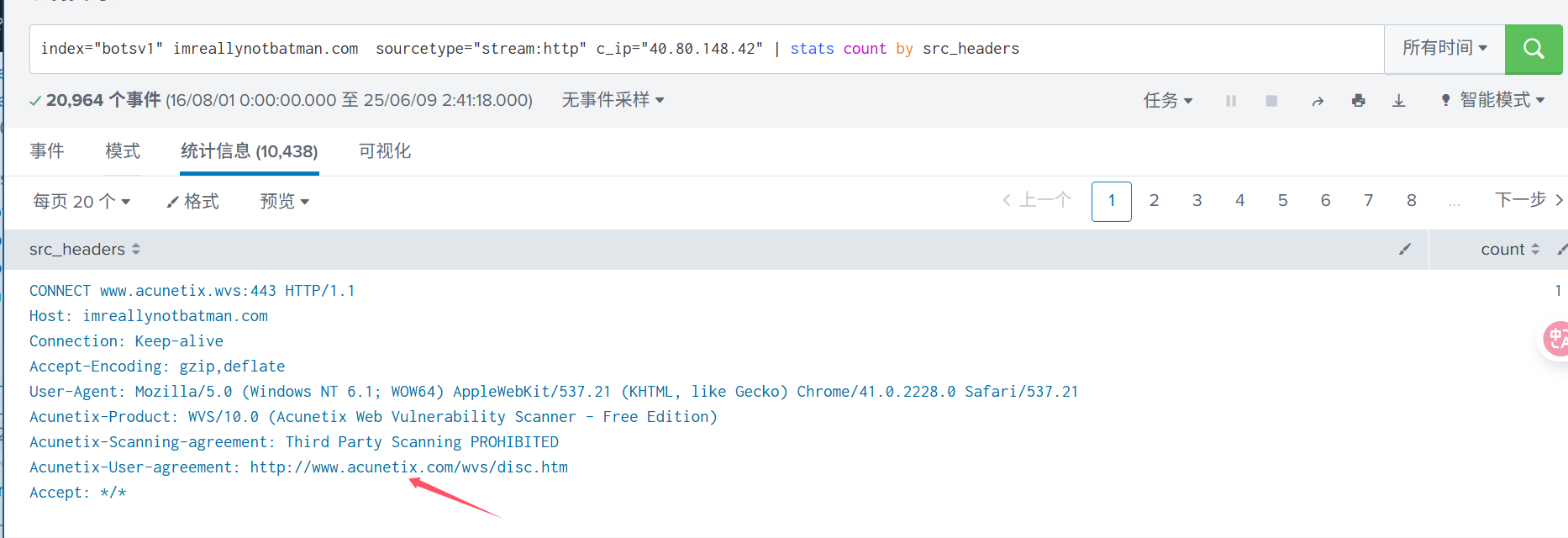
Q2: 扫描器的公司名叫什么?
查询语句: index=“botsv1” imreallynotbatman.com sourcetype=“stream:http” c_ip=“40.80.148.42” | stats count by src_headers
Q3: 用的是什么CMS(What content management system is imreallynotbatman.com likely using?)
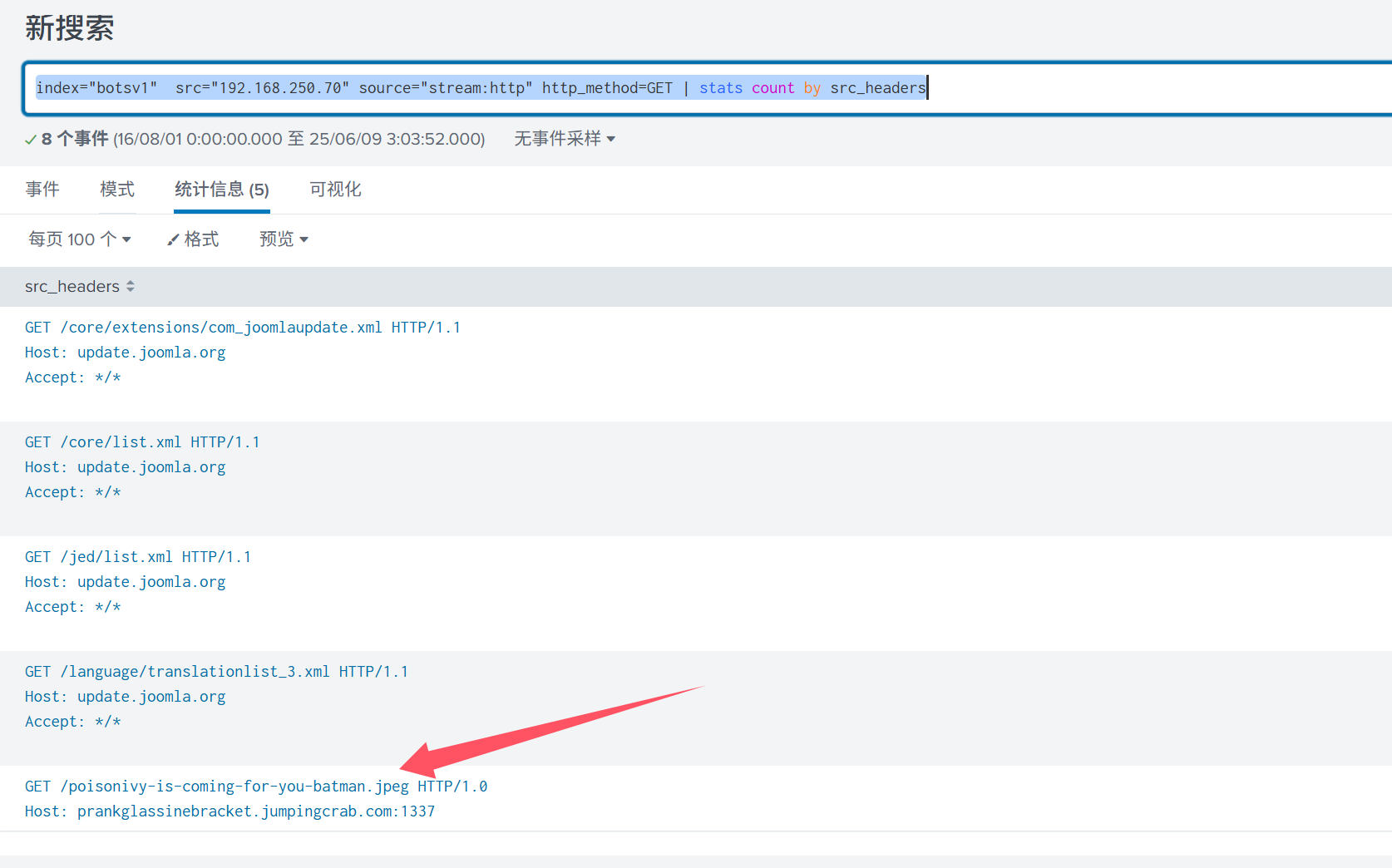
查询语句: index=“botsv1” imreallynotbatman.com sourcetype=“stream:http” cms | stats count by src_headers
明显是joomla
Q4: What is the name of the file that defaced the imreallynotbatman.com website? Please submit only the name of the file with extension?
找一个文件
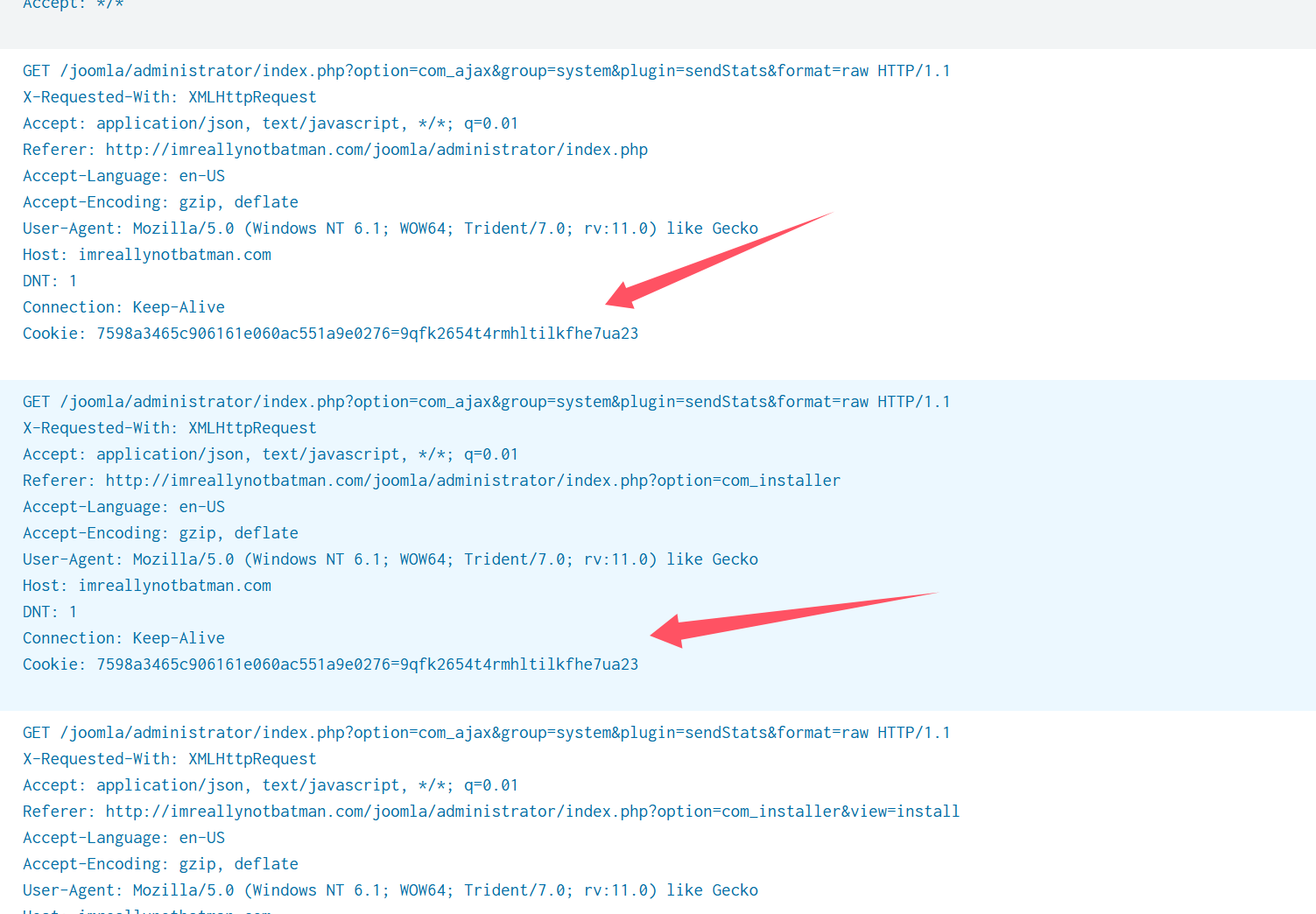
index=“botsv1” src=“192.168.250.70” source=“stream:http” http_method=GET | stats count by src_headers
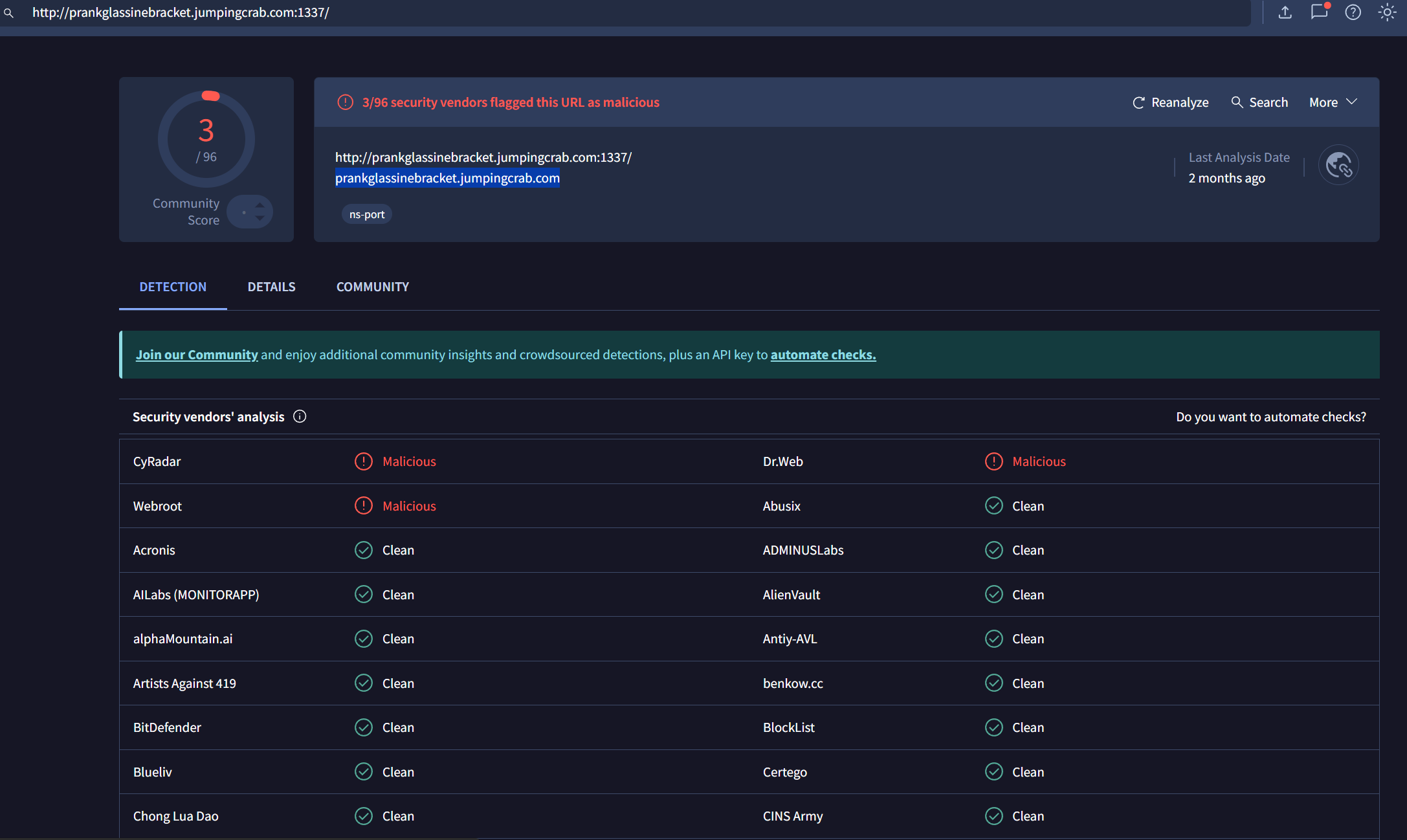
Q5: 恶意域名是什么?
接着上面的那个Host即可,vt查一下发现是恶意域名.
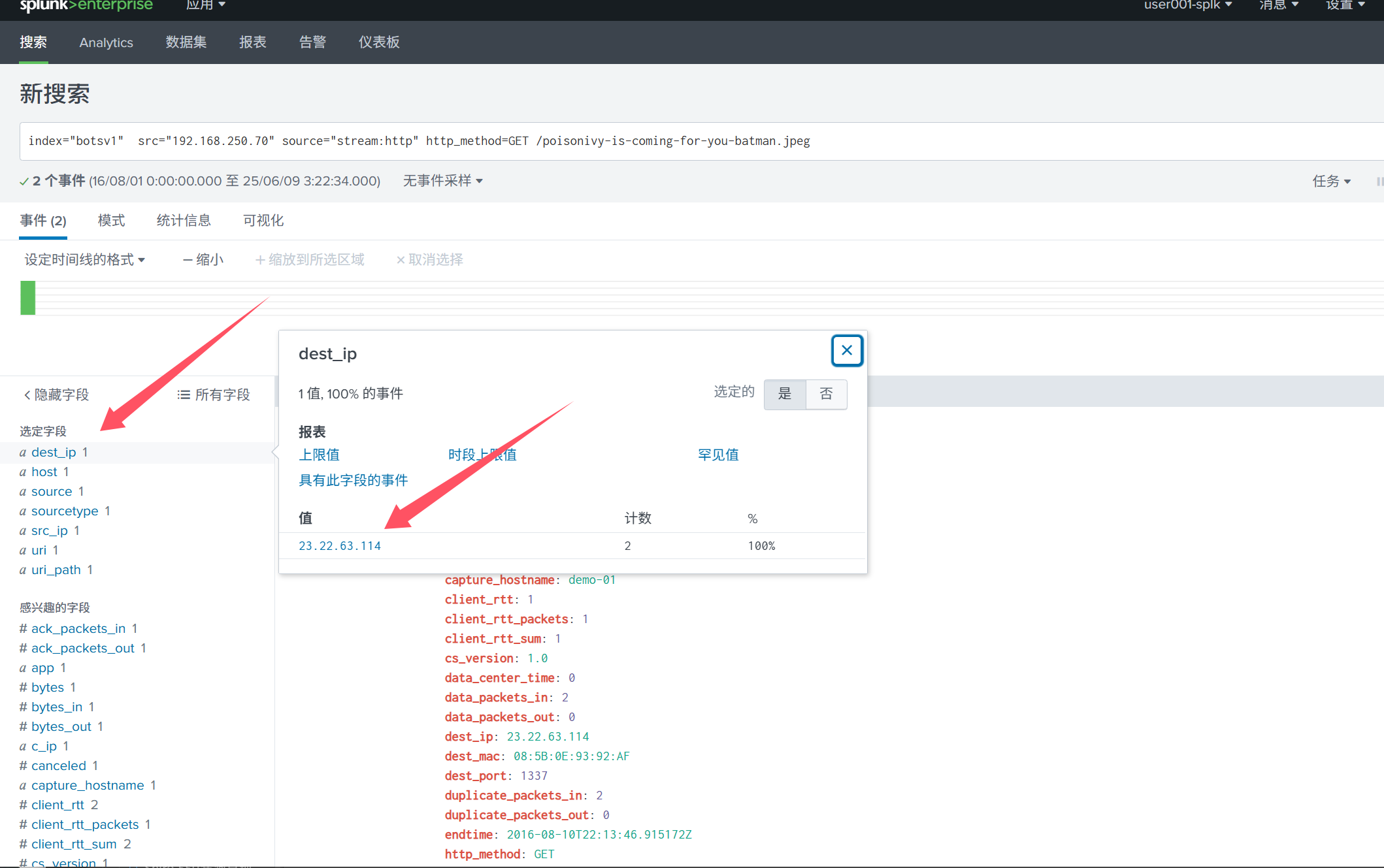
Q6:What IPv4 address has Po1s0n1vy tied to domains that are pre-staged to attack Wayne Enterprises?
直接搜前面那个图片即可
index=“botsv1” src=“192.168.250.70” source=“stream:http” http_method=GET /poisonivy-is-coming-for-you-batman.jpeg
Q8: What IPv4 address is likely attempting a brute force password attack against imreallynotbatman.com?(哪个ip在进行密码爆破)
先筛ip
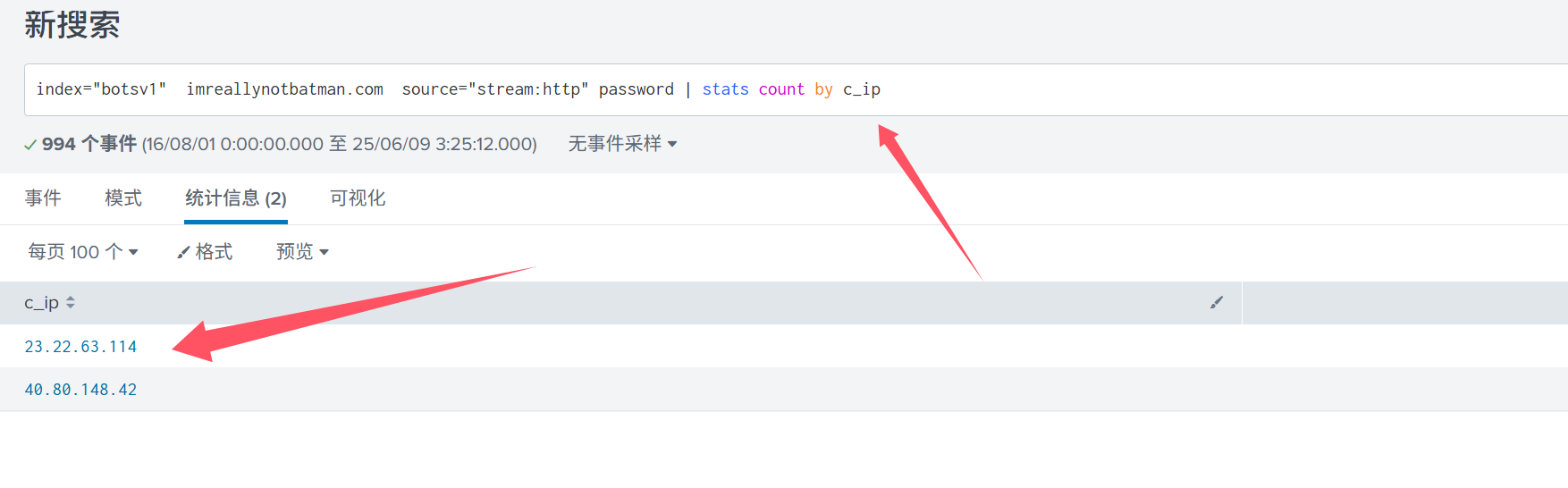
然后发现下面那个ip是扫描器的ip,过一下它即可
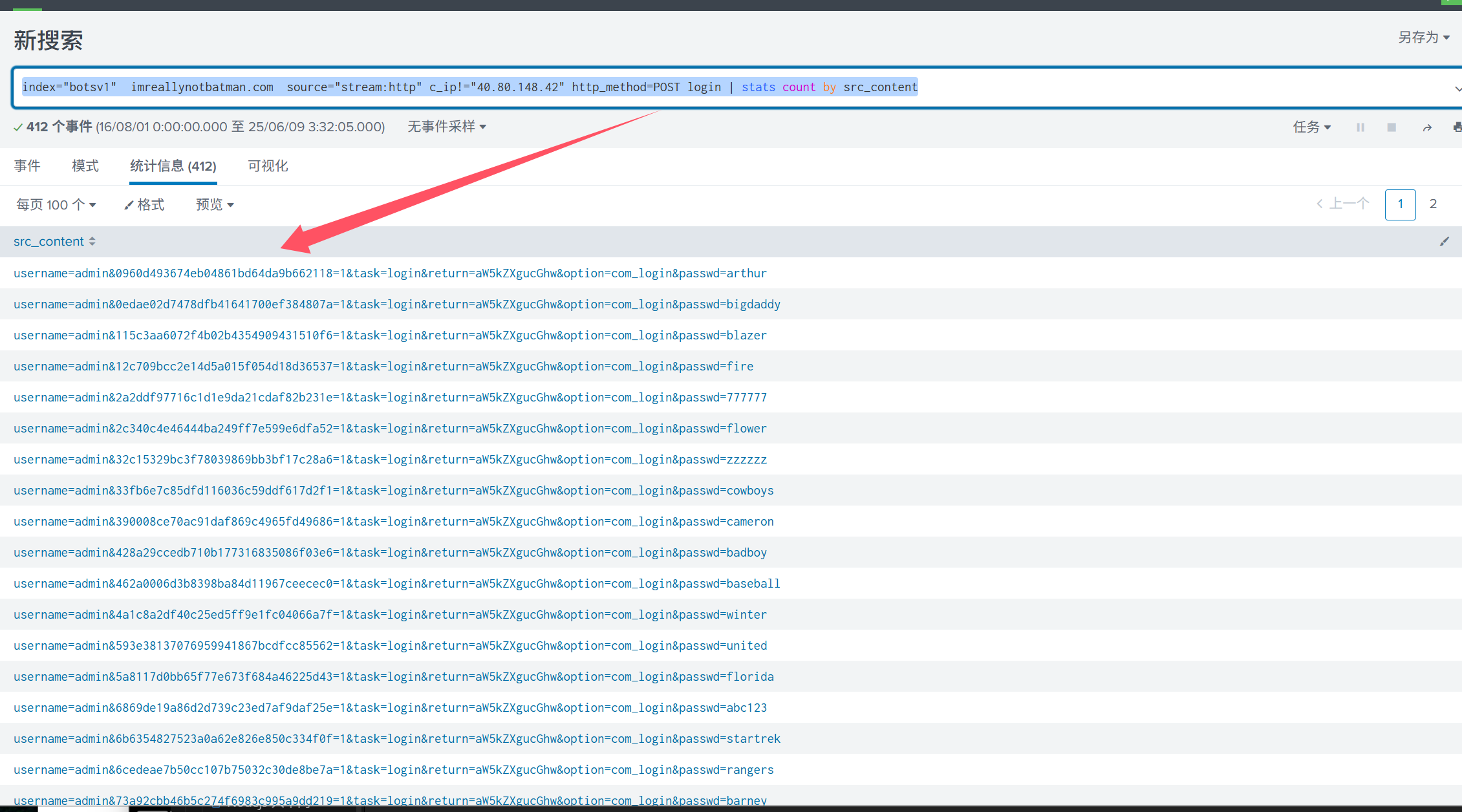
index=“botsv1” imreallynotbatman.com source=“stream:http” c_ip!=“40.80.148.42” http_method=POST login | stats count by src_content
答案是: 23.22.63.114
Q9: What is the name of the executable uploaded by Po1s0n1vy?(上传的可执行文件是什么)
index=“botsv1” dest_ip=192.168.250.70 source=“stream:http” http_method=POST .exe
3791.exe
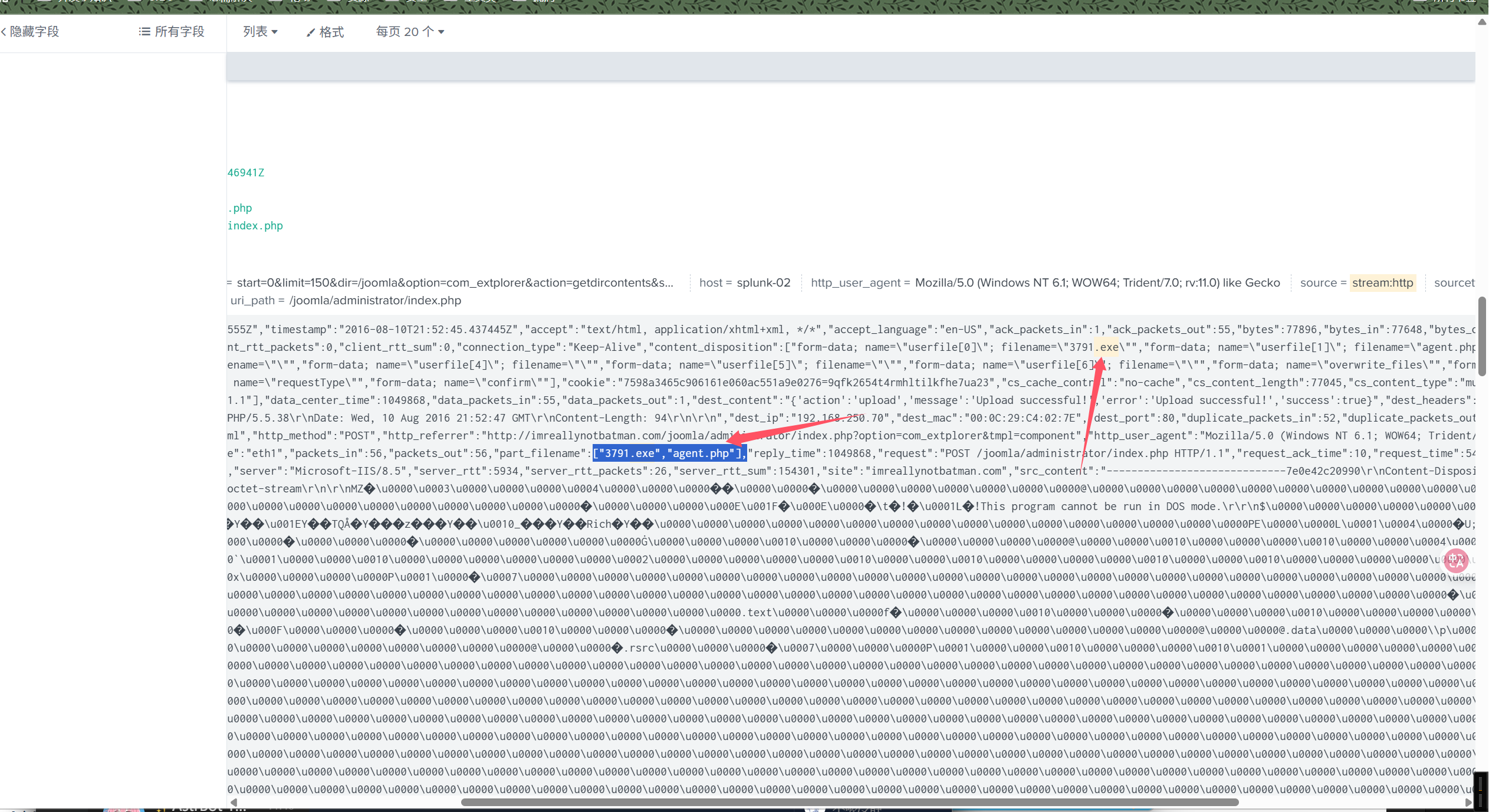
明显是这个
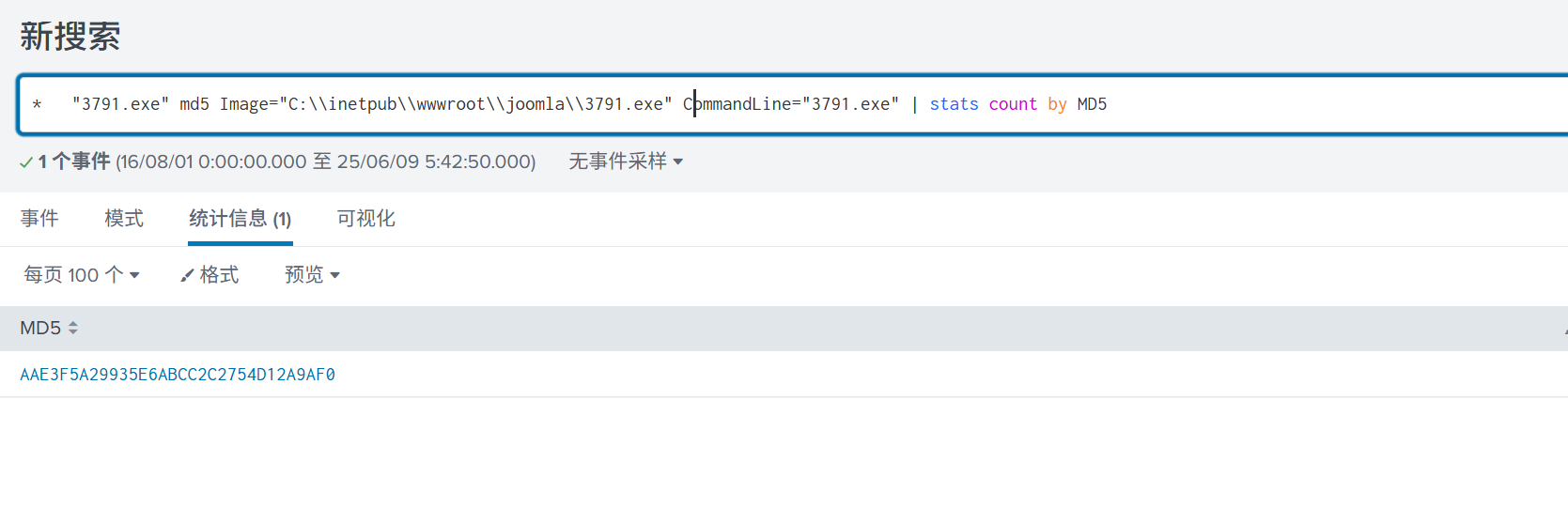
Q10: What is the MD5 hash of the executable uploaded?
“3791.exe” md5 Image=“C:\inetpub\wwwroot\joomla\3791.exe” CommandLine=“3791.exe” | stats count by MD5
AAE3F5A29935E6ABCC2C2754D12A9AF0
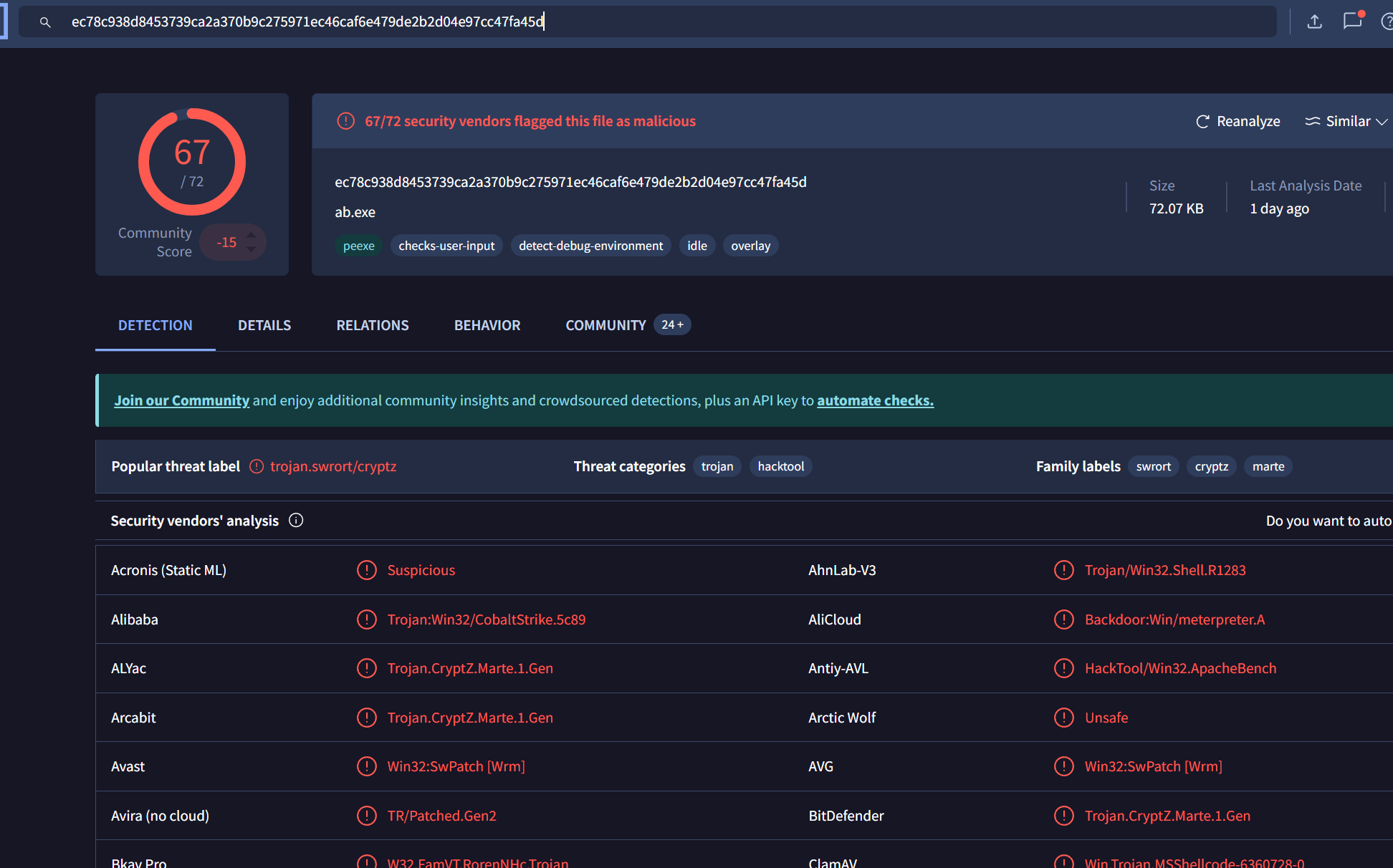
Q11: GCPD reported that common TTPs (Tactics, Techniques, Procedures) for the Po1s0n1vy APT group, if initial compromise fails, is to send a spear phishing email with custom malware attached to their intended target. This malware is usually connected to Po1s0n1vys initial attack infrastructure. Using research techniques, provide the SHA256 hash of this malware.(投放的恶意钓鱼邮件的文件SHA256值)
直接搜前面那个ip即可,然后通过关联找到对应的exe
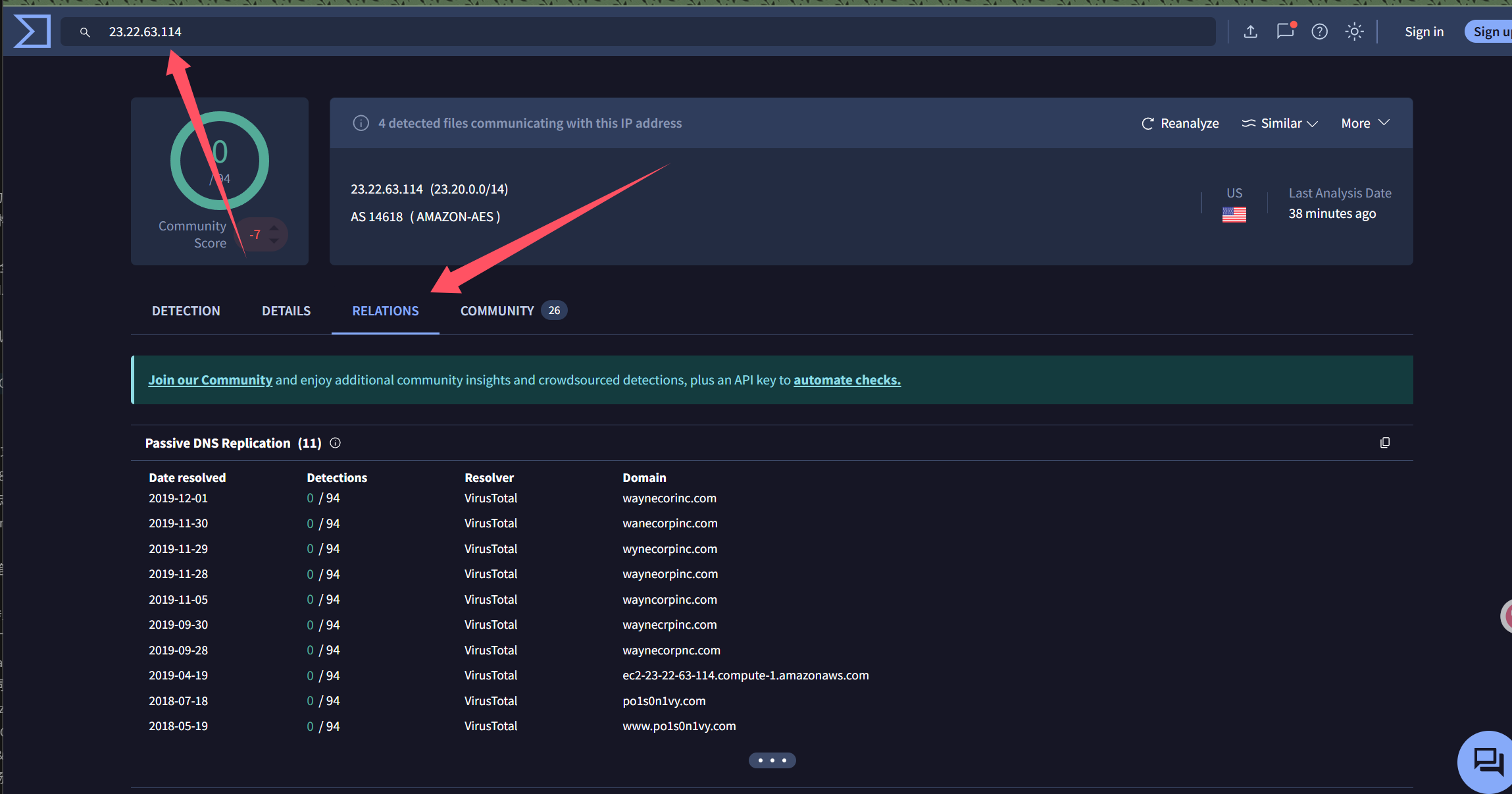
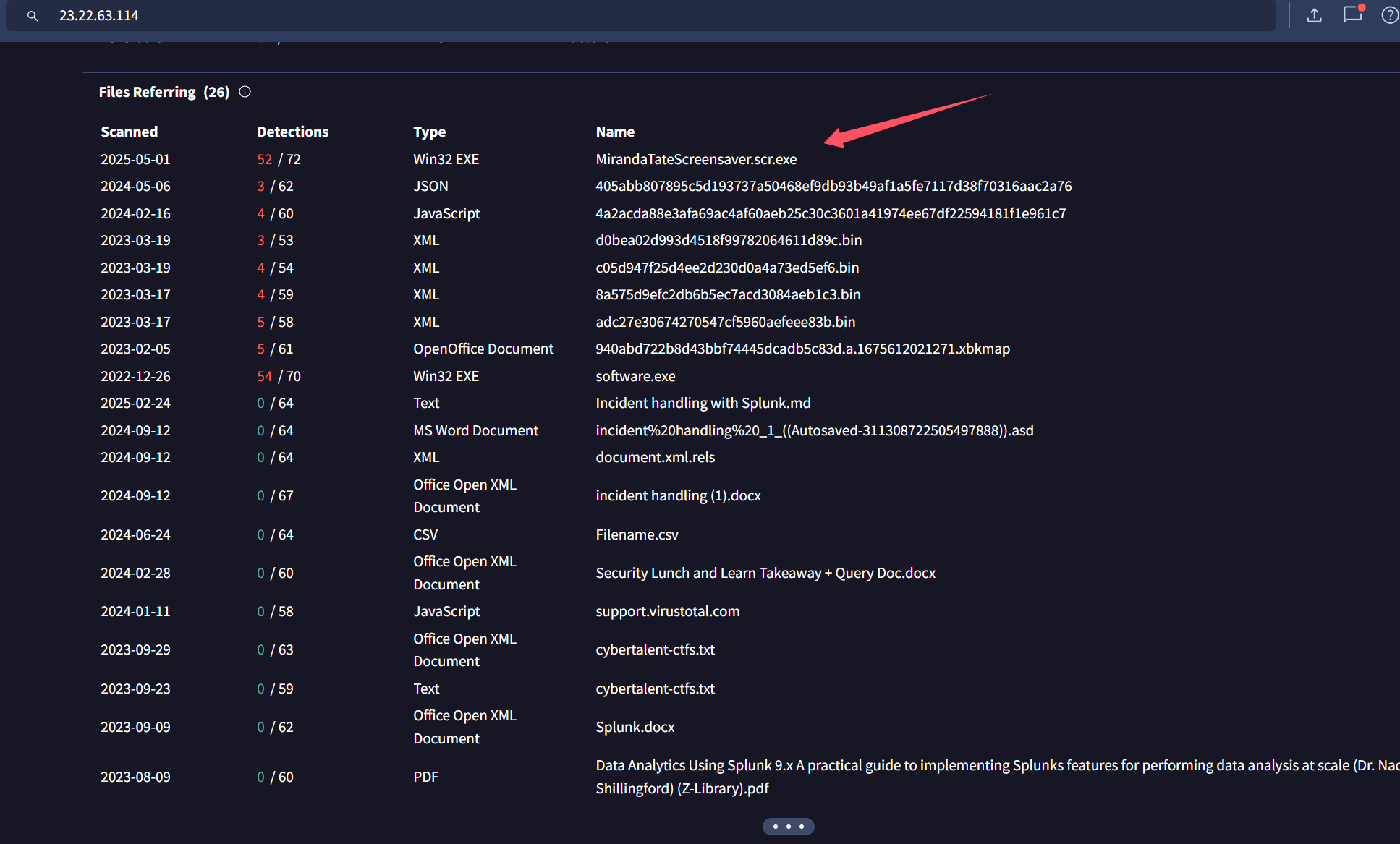
Q12: What special hex code is associated with the customized malware discussed in question 111?
翻评论区
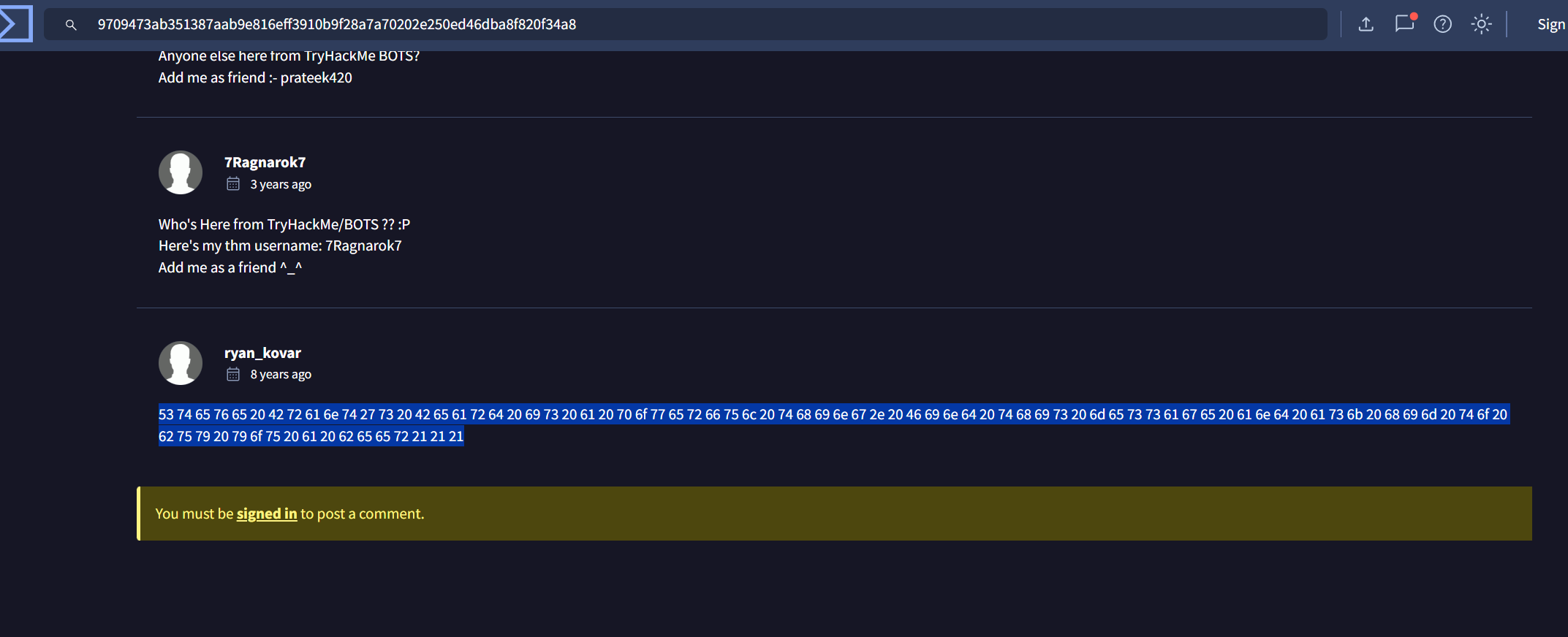
Q14: What was the first brute force password used?(最开始爆破的密码是什么)
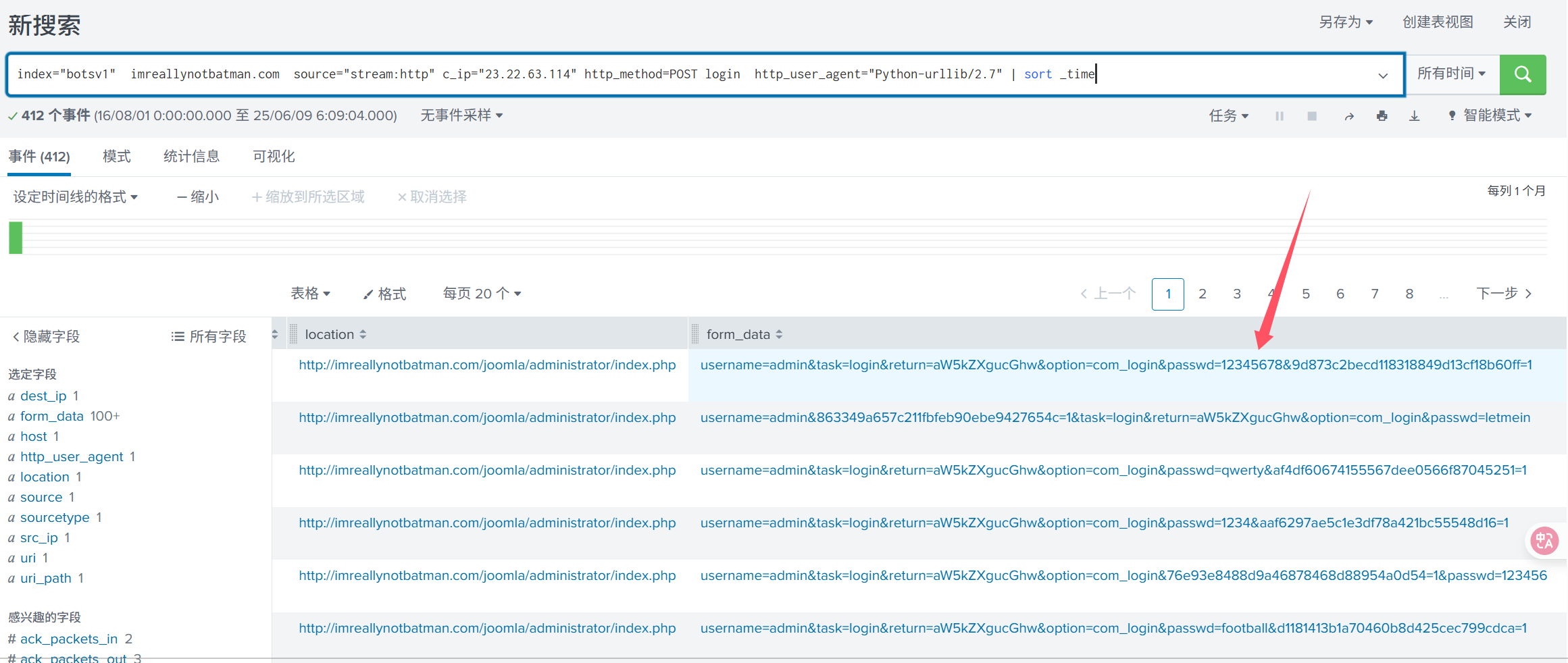
index=“botsv1” imreallynotbatman.com source=“stream:http” c_ip=“23.22.63.114” http_method=POST login http_user_agent=“Python-urllib/2.7” | sort _time
很显然是12345678
优化的查询语句:
1 | index="botsv1" imreallynotbatman.com source="stream:http" c_ip="23.22.63.114" http_method=POST login http_user_agent="Python-urllib/2.7" | rex "username=(?<username>\w+)&.*?passwd=(?<passwd>\w+)" |table username, _time passwd |dedup username, passwd | sort _time |
Q15: One of the passwords in the brute force attack is James Brodsky’s favorite Coldplay song. We are looking for a six character word on this one. Which is it?
Q16: What was the correct password for admin access to the content management system running “imreallynotbatman.com”?
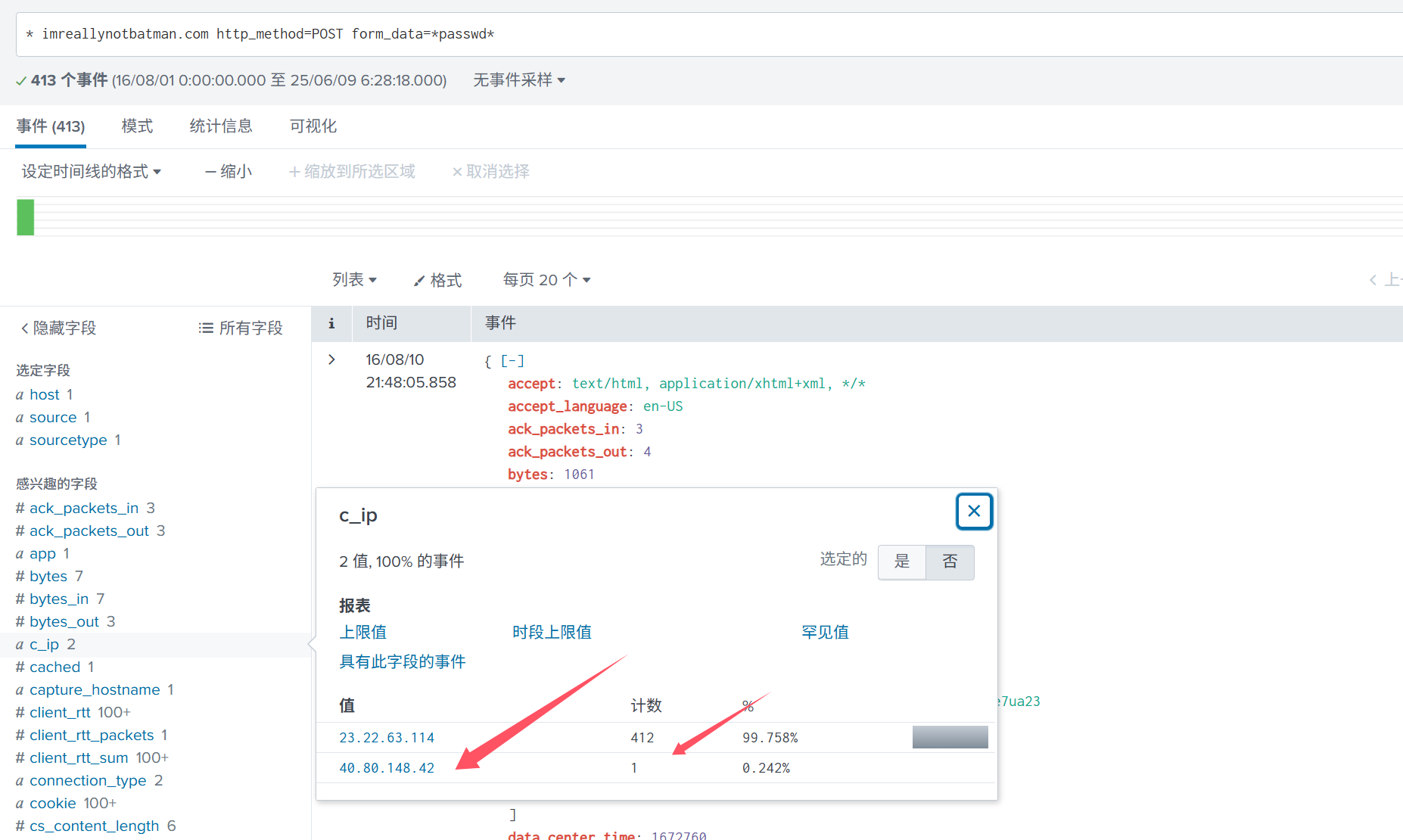
应该就是在另外这个ip 提交了唯一一次正确密码
-
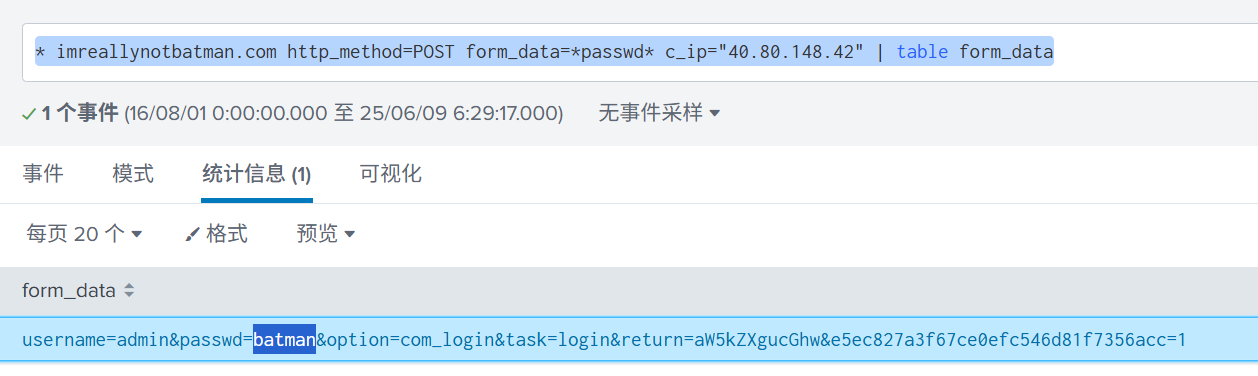
imreallynotbatman.com http_method=POST form_data=passwd c_ip=“40.80.148.42” | table form_data
batman
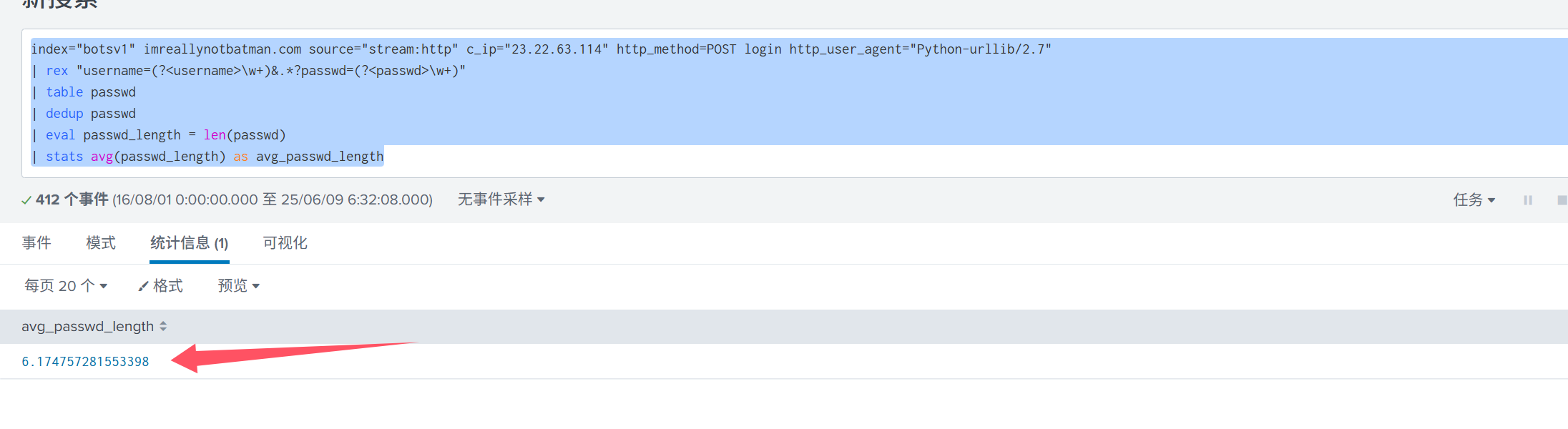
Q17: What was the average password length used in the password brute forcing attempt?(爆破密码的平均长度)
1 | index="botsv1" imreallynotbatman.com source="stream:http" c_ip="23.22.63.114" http_method=POST login http_user_agent="Python-urllib/2.7" |
前面提取了passwd字段,这次用 eval len取得总长度,再stats avg as取平均数进行展示即可答案为: 6
Q18: How many seconds elapsed between the time the brute force password scan identified the correct password and the compromised login?
1 | imreallynotbatman.com http_method=POST form_data="*username*passwd*" |
Q19: How many unique passwords were attempted in the brute force attempt?(尝试了多少个密码)
1 | index="botsv1" imreallynotbatman.com source="stream:http" c_ip="23.22.63.114" http_method=POST login http_user_agent="Python-urllib/2.7" |
dc(field) — Distinct Count:统计某字段中不重复的值的个数。
重点查询语句积累
-
筛选所选字段的包含我们想要的关键字的结果
1 | index=botsv1 sourcetype=stream:dns src_ip=192.168.250.100 |
-
计算长度
1 | index=botsv1 sourcetype="xmlwineventlog:microsoft-windows-sysmon/operational" *.vbs |
-
统计次数
1 | index=botsv1 sourcetype="stream:smb" src_ip=192.168.250.100 |